A Framework for Comparing Crypto Wallets
Introduction
Not your keys, not your coins is a common mantra in crypto, but managing your own keys can be surprisingly difficult, especially for people that don't have the time or inclination to properly choose and manage the correct approach. Even experts get it wrong from time to time. In 2023, hackers gained access to the private key belonging to Luke Dashjr, a longtime Bitcoin Core developer, and stole just about all of his bitcoin. If this is difficult even for experts, what should we recommend to regular people?
Convenience and Security During Everyday Use
When evaluating the security of a crypto wallet, one needs to look at many different factors including the protection it provides against various risk scenarios and the reliability of the backup and recovery methods. We'll discuss each of these points in detail later in this article, but to start with, let's reduce our analyses to two dimensions:
- Protection against device compromise (are you protected against malware and hackers?)
- Convenience for everyday use (how difficult is it to make transactions when you need to?)
The perfect wallet for regular people to use for everyday transactions should strike a balance between security and convenience.
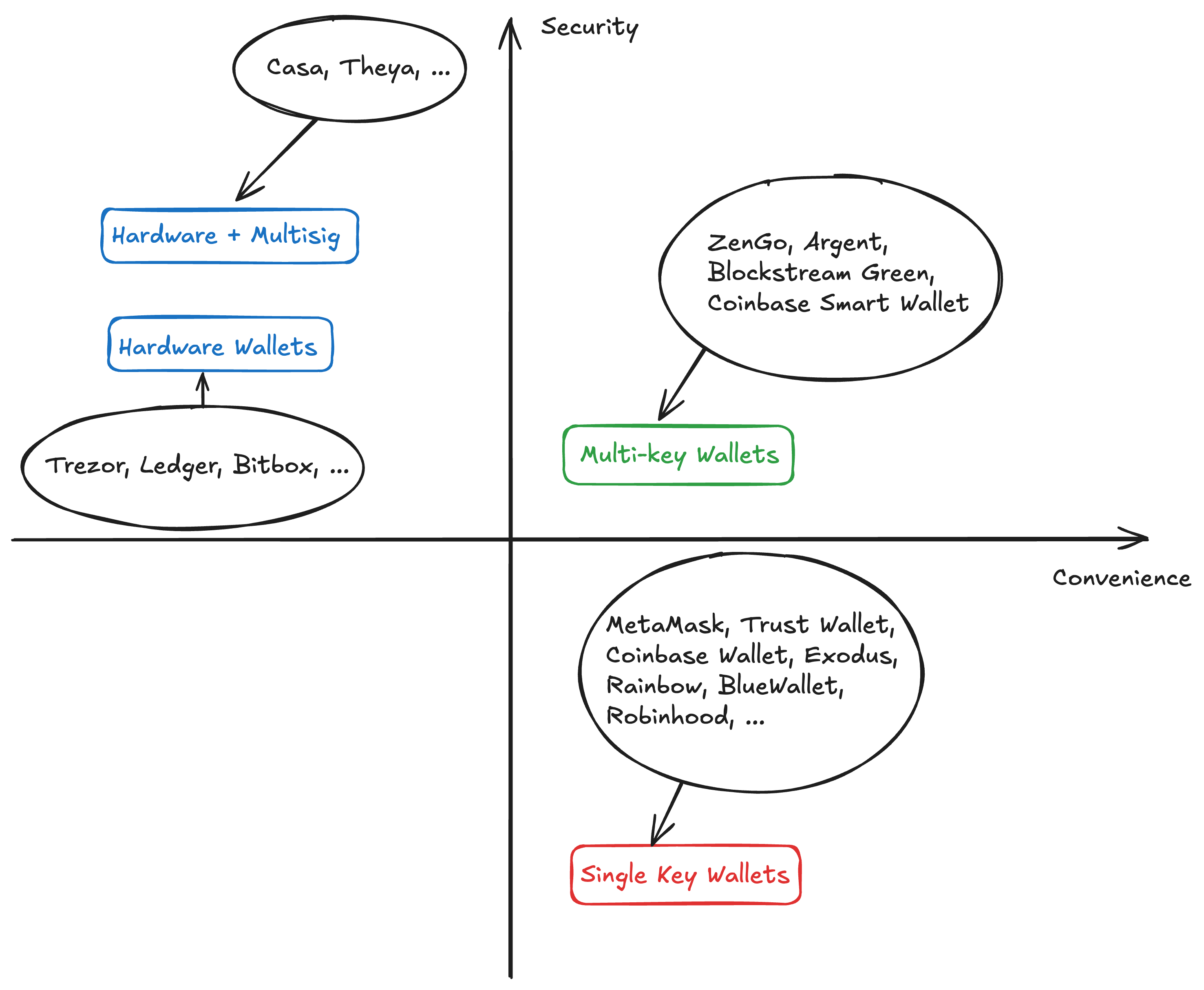
Figure 1: Security vs. convenience trade-offs for different wallet types
We've plotted the common types of crypto wallets against these two dimensions and through this lense, we provide a rating and overview for each of the types of crypto wallets below.
| Wallet Type | Everyday Use Convenience Rating | Protection Against Device Compromise |
|---|---|---|
| Single Key Wallet (e.g. MetaMask) | ★★★★★ | ★☆☆☆☆ |
| Hardware Wallet (e.g. Trezor) | ★★☆☆☆ | ★★★★☆ |
| Multi-Key Wallet (e.g. ZenGo) | ★★★★★ | ★★★★☆ |
| Multisig Hardware Wallet (e.g. Casa) | ★☆☆☆☆ | ★★★★★ |
| Secure Enclave/TTE Wallet (e.g. Turnkey) | ★★★★★ | ★★☆☆☆ |
Table 1: Wallet Type Comparison: Security and Convenience Ratings
Single Key Wallets (e.g. MetaMask)
As of November 2024, these are the most popular type of crypto wallet. Examples are MetaMask, Exodus, Phantom, Trust Wallet and Rainbow. There is a single private key on your device and this is backed up by writing down a seed phrase which can be used to recover your wallet.
-
Everyday Use Convenience: 5/5
- No physical hardware required, simple transaction approval process
- Easy access through user-friendly app with normal authentication methods (biometric/password)
- Can be used on multiple devices (by loading the seed phrase into each)
-
Protection Against Device Compromise: 1/5
- Vulnerable to malware
- Typically limited transaction analysis or warning systems
- No system to lock the wallet if your device is compromised
Hardware Wallets (e.g. Trezor)
Hardware wallets are widely used and recommended by crypto enthusiasts. These are Physical devices (like Ledger or Trezor) that store your private keys offline, isolated from internet-connected devices. While still using a single key and seed phrase backup, they provide significantly better security than software wallets by keeping keys away from potential malware or remote attacks.
-
Everyday Use Convenience: 2/5
- Requires physical access to device
- Must connect hardware to computer/phone
- Multiple steps for transaction approval which require switching between the companion app and the hardware wallet interface
- Cannot transact without physical device present
-
Protection Against Device Compromise: 4/5
- Protected against malware and software based attacks as your private keys never leave the device and the hardware wallet is isolated from your computer or mobile phone which is connected to the internet
- Resistant to phishing as the user needs to explicitly check transaction details on the hardware device
- Potential vulnerability to supply chain attacks or backdoors if purchasing from unauthorized resellers or if manufacturer is compromised
Multi-Key Wallets (e.g. ZenGo)
Multi-key wallets distribute control of your funds across multiple parties for better security. Examples include ZenGo, which splits your key between your device and their servers - this means you can't lose access by forgetting a seed phrase, and attackers would need to hack both your device and ZenGo's servers to steal funds.
-
Everyday Use Convenience: 5/5
- No physical hardware required, simple transaction approval process
- Easy access through user-friendly app with normal authentication methods (usually biometrics)
- Works across multiple devices without needing to import and export seed phrases
- Read-only access can be provided where transactions can be initiated by one device and approved by another
-
Protection Against Device Compromise: 4/5
- Distributed key storage prevents single point of failure
- Device compromise alone cannot expose private keys
- Built-in transaction analysis and fraud detection
- Additional security layer through server-side verification
Multisig Hardware Wallets (e.g. Casa)
Multisig hardware wallets combine the security benefits of hardware wallets with additional protection through multiple device requirements. These solutions require two or more hardware devices to approve transactions, and services like Casa make the setup and management more user-friendly. This approach provides the highest level of security by protecting against both device compromise and seed phrase theft.
-
Everyday Use Convenience: 1/5
- Requires multiple devices for authorization
- Longer transaction approval process as one need to coordinate between devices
- Limited mobility due to hardware requirements
-
Protection Against Device Compromise: 5/5
- Multiple devices must be compromised to lose funds
- Geographic distribution of keys possible
- Hardware-level security on multiple devices
- Built-in time delays for large transactions
- Professional security team monitoring (in some cases)
- Supply chain/backdoor risks are mitigated since an attacker would need to compromise multiple devices from different manufacturers
Secure Enclave/TTE Wallets (e.g. Turnkey)
Secure Enclave and Trusted Transaction Environment (TTE) wallets leverage hardware-level security features and isolated execution environments in modern cloud infrastructure. Examples include Turnkey and Magic, which store and process private keys in highly secure environments with strict access controls, policy enforcement, and comprehensive audit logging.
-
Everyday Use Convenience: 5/5
- No physical hardware required, simple transaction approval process
- Easy access through user-friendly interfaces
- Can be used on multiple devices
-
Protection Against Device Compromise: 2/5
- Keys are stored in hardware security modules (HSMs) or secure enclaves
- Professional security monitoring and access controls
- Still relies on single key architecture, but with enhanced security measures
- While theoretically verifiable that provider/employees cannot access keys, this verification is technically complex and impractical for most users
Risk Scenario Overview
If you decide to move your funds off exchanges, ideally you should be able to go to sleep at night knowing you are protected against the most important risks. To help evaluate different options, we've divided wallets into 4 categories:
Let's compare some of the protection offered by each of these crypto wallet types for the most common risk scenarios.
| Wallet Type | Device is hacked or gets a virus | Device is stolen | Device is lost | Wallet provider shuts down or blocks access |
|---|---|---|---|---|
| Single Key Wallet (e.g. MetaMask) | ★☆☆☆☆ | ★☆☆☆☆ | ★★★☆☆ | ★★★☆☆ |
| Multi-Key Wallet (e.g. ZenGo) | ★★★★☆ | ★★★★★ | ★★★★★ | Depends on implementation |
| Hardware Wallet (e.g. Trezor) | ★★★★☆ | ★★★★★ | ★★★☆☆ | ★★★★★ |
| Multisig Hardware Wallet (e.g. Casa) | ★★★★★ | ★★★★★ | ★★★★★ | ★★★★★ |
| Secure Enclave/TTE Wallet (e.g. Turnkey) | ★★☆☆☆ | ★★★★☆ | ★★★★☆ | Depends on implementation |
Table 2: Risk Protection Comparison Across Wallet Types
*The ratings above are provided for a typical configuration of each of the above types of wallets and the reasoning for each rating is given below.
1. Your mobile phone or computer is hacked or gets a virus
Single Key Wallet: The hacker or malware will immediately get access to your private key and gain access to your funds. While these wallets often take steps to make this more difficult, such as storing the private key on the secure enclave of your device, if your device is compromised, there is a strong chance that the attacker will find a way to steal your funds. Rating: 1/5
Multi-Key Wallet: Provides significantly better protection against hacks because the private key is split across multiple locations. Even if malware compromises your device, the attacker would need to breach additional authentication factors or locations to access your funds. The distributed nature of the security makes it much harder for any single point of failure to result in loss of funds. Rating: 4/5
Hardware Wallet: Private keys never leave the device and all transactions must be physically confirmed, so malware on your computer or phone cannot compromise your funds. The physical separation provides a strong defense against digital attacks. Rating: 4/5
Multisig Hardware: Provides the highest level of security against device compromise. Not only do they have the hardware wallet's immunity to malware, but they also require multiple independent devices to authorize any transaction. Rating: 5/5
Secure Enclave/TTE Wallet: Provides moderate protection through hardware-level security features and professional monitoring. While more secure than basic single-key wallets, they still rely on a single key architecture. The security depends heavily on the implementation quality and operational security of the provider. While theoretically verifiable that the provider/employees cannot access keys, this verification is technically complex and impractical for most users. Rating: 2/5
2. Device containing your crypto wallet is stolen
Single Key Wallet: A stolen device could potentially give the thief access to your funds if they can bypass the device's security measures. The main protection here is your device's lock screen and any additional wallet-specific security measures like passwords or biometrics. Rating: 1/5
Multi-Key Wallet: Offers robust protection against physical theft since the thief would need additional authentication factors beyond just the device itself. The distributed key storage means physical access to one device is insufficient to compromise funds. Rating: 5/5
Hardware Wallet: Requires a PIN code to access, and typically locks itself after several incorrect attempts. Even with physical possession, a thief cannot access funds without knowing the PIN code. Rating: 5/5
Multisig Hardware: Provides maximum protection since the thief would need to obtain multiple devices and know how to use them together. The requirement for multiple independent authorizations makes theft-based attacks extremely difficult. Rating: 5/5
Secure Enclave/TTE Wallet: Offers good protection through hardware security modules and access controls. Physical device theft alone is typically insufficient to compromise funds due to additional authentication requirements and security policies. Rating: 4/5
3. Device containing your crypto wallet is lost
Single Key Wallet: Recovery depends entirely on having access to a correct backup. If using cloud backup, users must remember their backup encryption password. If using a seed phrase, it must be stored securely and accessibly. If either the password is forgotten or the seed phrase is lost/damaged, funds become permanently inaccessible. Rating: 3/5
Multi-Key Wallet: Offers superior protection against device loss through provider-assisted recovery options. Even if a user forgets their password or loses access to their device, they can typically recover their wallet through a combination of identity verification and provider assistance. This eliminates the single point of failure present in self-managed backups. Rating: 5/5
Hardware Wallet: Can be recovered using the seed phrase backup, but face the same risks as single key wallets regarding seed phrase management. Rating: 3/5
Multisig Hardware: Multiple recovery paths and backup options provide redundancy, though requires careful management of multiple seed phrases or key shares. Rating: 5/5
Secure Enclave/TTE Wallet: Recovery mechanisms vary by implementation but typically include robust backup procedures and professional key management. Most solutions offer multiple recovery paths and maintain encrypted backups. Rating: 4/5
4. Wallet provider shuts down or blocks access
Single Key Wallet: While theoretically independent of the provider, recovery still depends on having access to either a correctly stored and accessible seed phrase or a cloud backup with a remembered encryption password. If either of these fails, funds cannot be recovered even if the wallet software itself is still functional. Rating: 3/5
Multi-Key Wallet: The level of protection varies by implementation:
- Basic implementations rely entirely on provider servers to function, making funds completely inaccessible if the provider shuts down without warning. Rating: 0/5
- More robust implementations include emergency backup procedures such as:
- Encrypted backups stored in user-controlled cloud storage (e.g., iCloud, Google Drive)
- Optional backup of decryption keys with trusted third parties
Hardware Wallet: While the official software may become unavailable, funds remain accessible through various third-party wallet software that supports the device. The seed phrase ensures funds are always recoverable. Rating: 5/5
Multisig Hardware: Similar to regular hardware wallets, funds remain accessible through alternative software that supports the multisig setup, with seed phrases ensuring recoverability. Rating: 5/5
Secure Enclave/TTE Wallet: The level of protection varies by implementation:
- Basic implementations rely entirely on provider servers to function, making funds completely inaccessible if the provider shuts down without warning. Rating: 0/5
- More robust implementations include emergency backup procedures such as:
- Encrypted backups stored in user-controlled cloud storage (e.g., iCloud, Google Drive)
- Optional backup of decryption keys with trusted third parties
Understanding Crypto Wallet Backup Methods
When it comes to crypto wallet security, your backup method is just as important as the wallet type you choose. Let's dive into the different backup approaches available and understand their strengths and limitations.
Backup method summary
| Backup Method | Convenience | Security | Human Error Protection | Provider Shutdown Protection |
|---|---|---|---|---|
| Seed Phrase | ★★☆☆☆ | ★★☆☆☆ | ★☆☆☆☆ | Yes |
| Cloud Backup (Provider-assisted) | ★★★★★ | ★★★★☆ | ★★★★★ | No** |
| Cloud Backup (User-encrypted) | ★★★★☆ | ★★★★☆ | ★★☆☆☆ | Yes |
| Social Recovery | ★★★☆☆ | ★★★★☆ | ★★★☆☆ | Yes |
| Multiple Device Recovery | ★★☆☆☆ | ★★★★★ | ★★★☆☆ | Yes |
Table 3: Comparison of Backup Methods Across Wallet Types
*Ratings given are from the perspective of the average user. This can be subjective, but the reasoning behind the ratings are given below.
**Provider-assisted cloud backups can be used in conjunction with other backup methods, like user-encrypted cloud backup and multiple device recovery to provide protection against provider shutdown.
Let's discuss each of the above backup methods.
Seed Phrase Backup
Used by: Single Key Wallets, Hardware Wallets, Multisig Hardware Wallets
The traditional seed phrase method involves writing down 12-24 words in a specific order. With hardware wallets and most popular single-key wallets this is the default option. While this approach offers strong security if done correctly, it's surprisingly fragile in practice. Users often lose the phrase, write it down incorrectly, or store it insecurely.
Unfortunately most humans are not good at guarding seed phrases against loss or theft. That's not to say that there aren't people who are very good at it for whom this backup method can be a perfect fit. For example, see Jameson Lopp's reviews of how various metal seed plates fare in disaster scenarios.
- Convenience: 2/5 - The process is cumbersome and requires careful handling
- Security: 4/5 - Very secure when stored properly, but vulnerable to physical theft
- Recovery Success: 1/5 - High failure rates from loss, damage, or user error
- Safe against provider shutdown: Yes, as long as the seed phrase is stored securely.
Cloud Backup (User-encrypted)
Used by: Single Key Wallets, Multi-key Wallets
To improve ease-of use and reduce potential for loss, many single key and multi-key wallets allow user-encrypted cloud backups. Users can encrypt their wallet backup with a password and store it in cloud storage like Google Drive or iCloud Drive. The encrypted backups can even be stored in multiple places for increased reliability. While convenient, recovery depends entirely on remembering or safely storing the encryption password.
- Convenience: 4/5 - Simple but requires password management
- Security: 4/5 - Strong encryption but depends on password strength
- Recovery Success: 3/5 - Lost if user forgets password
- Safe against provider shutdown: Yes, but requires user to remember their password and have access to the cloud storage they used for backup.
Cloud Backup (Provider-assisted)
Used by: Multi-Key Wallets
A strong advantage of multi-key wallets is that the provider can is that the provider can store the decryption key for a user's personal cloud backups. When compared to user-encrypted cloud backups eliminates the risk of the user not being able to recover funds due a forgotten or lost password. However, ideally provider-assisted cloud backups should always be combined with an additional backup method that protects against provider shutdown.
- Convenience: 5/5 - Works seamlessly in the background
- Security: 4/5 - Strong encryption and professional security practices
- Recovery Success: 5/5 - Professional support makes recovery highly reliable
- Safe against provider shutdown: No - This backup method must be combined with another backup method like user-encrypted cloud-backups
Social Recovery
Used by: Multi-Key Wallets
This approach lets you designate trusted friends or family as "guardians" who can help recover your wallet. It can be an excellent backup and recovery method when implemented correctly, Vitalik Buterin has written an article advocating for wider spread adoption of this approach. However, it's not for everyone as it requires careful planning with regards to who to add as guardians. If not managed correctly, there is a risk that guardians might collude to lock you out of your own wallet or that guardians might not be accessible when you need to recover your wallet.
- Convenience: 3/5 - Requires initial setup with guardians. Not everyone has friends and family readily available that meet the requirements
- Security: 4/5 - Highly secure due to distributed trust, but could be less secure if a set of untrusted and/or unreliable guardians are chosen
- Recovery Success: 4/5 - Works well if guardians remain accessible
- Safe against provider shutdown: Yes, typically strong protection for this scenario.
Multiple Device Recovery
Used by: Multisig Hardware Wallets, Multi-Key Wallets
This method requires multiple devices to authorize recovery, similar to how a bank vault might need two keys to open. While very secure, it adds complexity to the backup process.
- Convenience: 2/5 - Managing multiple devices can be challenging
- Security: 5/5 - Maximum security through hardware separation
- Recovery Success: 3/5 - More points of potential failure
- Safe against provider shutdown: Yes, typically strong protection for this scenario
Conclusion: Beyond "Not Your Keys, Not Your Coins"
After diving deep into the various types of crypto wallets, it's clear that the industry needs to move beyond simplistic security mantras. The reality is more nuanced, and the best solution depends heavily on your technical expertise, usage patterns, and security needs.
The Evolution of Wallet Security
While single-key wallets like MetaMask played a crucial role in making crypto accessible, their security model shows significant limitations in today's threat landscape. When a single compromised device or misplaced seed phrase can lead to complete loss of funds, we need to consider more robust alternatives.
For Newcomers and Regular Users
Multi-key wallets offer a compelling balance of security and usability:
- Strong protection against device compromise
- Multiple recovery options beyond seed phrases
- Familiar user experience for everyday transactions
- Built-in safeguards against common mistakes
This makes them an excellent choice for those entering the crypto space or anyone who values practical security.
For Advanced Users
Hardware wallets and multisig setups can provide excellent security when used correctly:
- Maximum control over your private keys
- Strong protection against online threats
- Ideal for long-term storage of larger amounts
However, these solutions require careful consideration:
- Commitment to proper security practices
- Thorough backup management
- Regular testing of recovery procedures
Looking Forward
The wallet landscape continues to evolve, with multi-key solutions leading the way toward better security models that don't sacrifice usability. The future of crypto security isn't about choosing between convenience and protection – it's about finding solutions that offer both.
The most secure wallet isn't necessarily the one with the most features or the strongest theoretical security model. It's the one that provides robust protection while being simple enough to use correctly every time. For many users, this means choosing a well-designed multi-key wallet that aligns with their technical comfort level and usage patterns.